AdminUI for OpenIddict: A gentle introduction
/ 6 min read
A quick journey back in time
If you’ve been around the ASP.NET world for more than 10 years, you may remember ASP.NET Membership - the predecessor of ASP.NET Identity. ASP.NET Membership was added in ASP.NET 2.0 as a way for developers to easily add authentication and authorization to their applications.
It was succeeded by ASP.NET Identity with the introduction ASP.NET MVC 5 in late 2013. ASP.NET Identity was a much more flexible system than ASP.NET Membership and, among other things, decoupled from the underlying storage mechanism. Over the years ASP.NET Identity has gone through various iterations, leaving us with it in its current form.
ASP.NET Membership came with an administration tool, called the Web Site Administration Tool (WSAT), which allowed you to manage users and roles, along with other application settings.
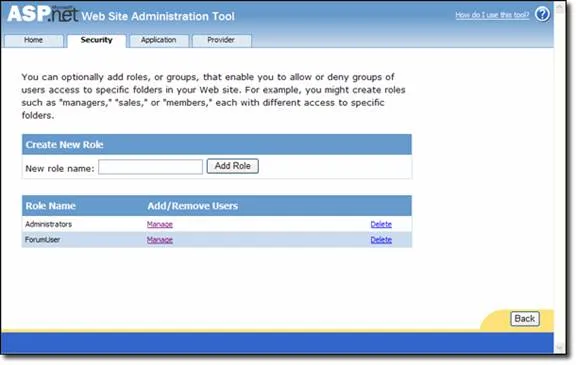
Sadly, Microsoft never provided anything similar for ASP.NET Identity.
Which brings us to AdminUI
This brings me today and to the topic of this blog post, which is a tool called AdminUI for OpenIddict. AdminUI is developed by a company in the UK called Rock Solid Knowledge (RSK) and is part of a suite of tools aimed at OpenIddict.
RSK has an equivalent (albeit more expansive) suite of tools aimed at Duende Identity Server. That suite of tools includes a similarly named AdminUI for Duende which is aimed at Duende Identity Server.
In this blog post, I want to give you a brief introduction to AdminUI for OpenIddict. Going forward, I will refer to it simply as AdminUI.
An overview of AdminUI
I see AdminUI as a spiritual successor to WSAT for ASP.NET Membership in that it provides a lot of the same functionality around managing users, roles, and other application settings.
For the purpose of this blog post, I will stick with a basic overview of the AdminUI user interface, rather than walk you through implementing it. The AdminUI documentation contains an installation section, which walks you through either manually adding Admin UI to existing application, or using their All-In-One template.
I created a demo project following their All-In-One template documentation. I will be using the project created by the template during the rest of this blog post.
Managing ASP.NET Identity configuration
Since AdminUI is aimed at managing OpenIddict configuration, and OpenIddict is concerned with user authentication and authorization, being able to administer users and roles is table stakes.
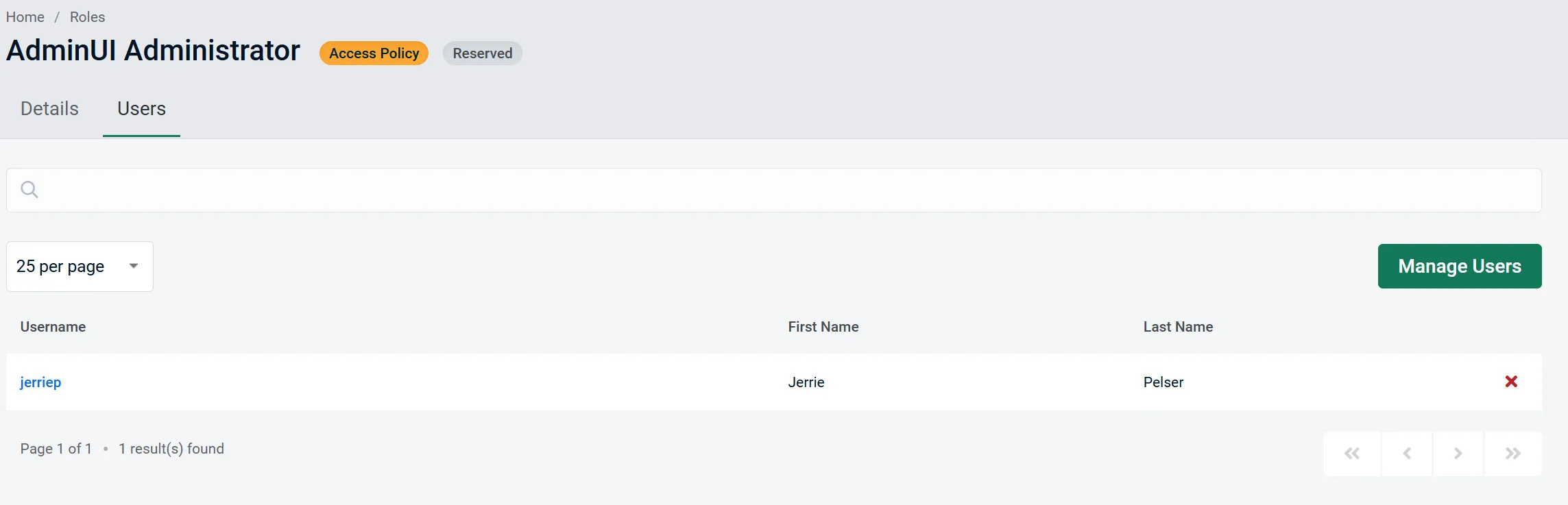
AdminUI gives you all the necessary tools to manage basic user information, control account lockout, assign roles, assign claims, and manage user access to application features. In short, everything you can do with ASP.NET Identity in an easy to navigate UI.
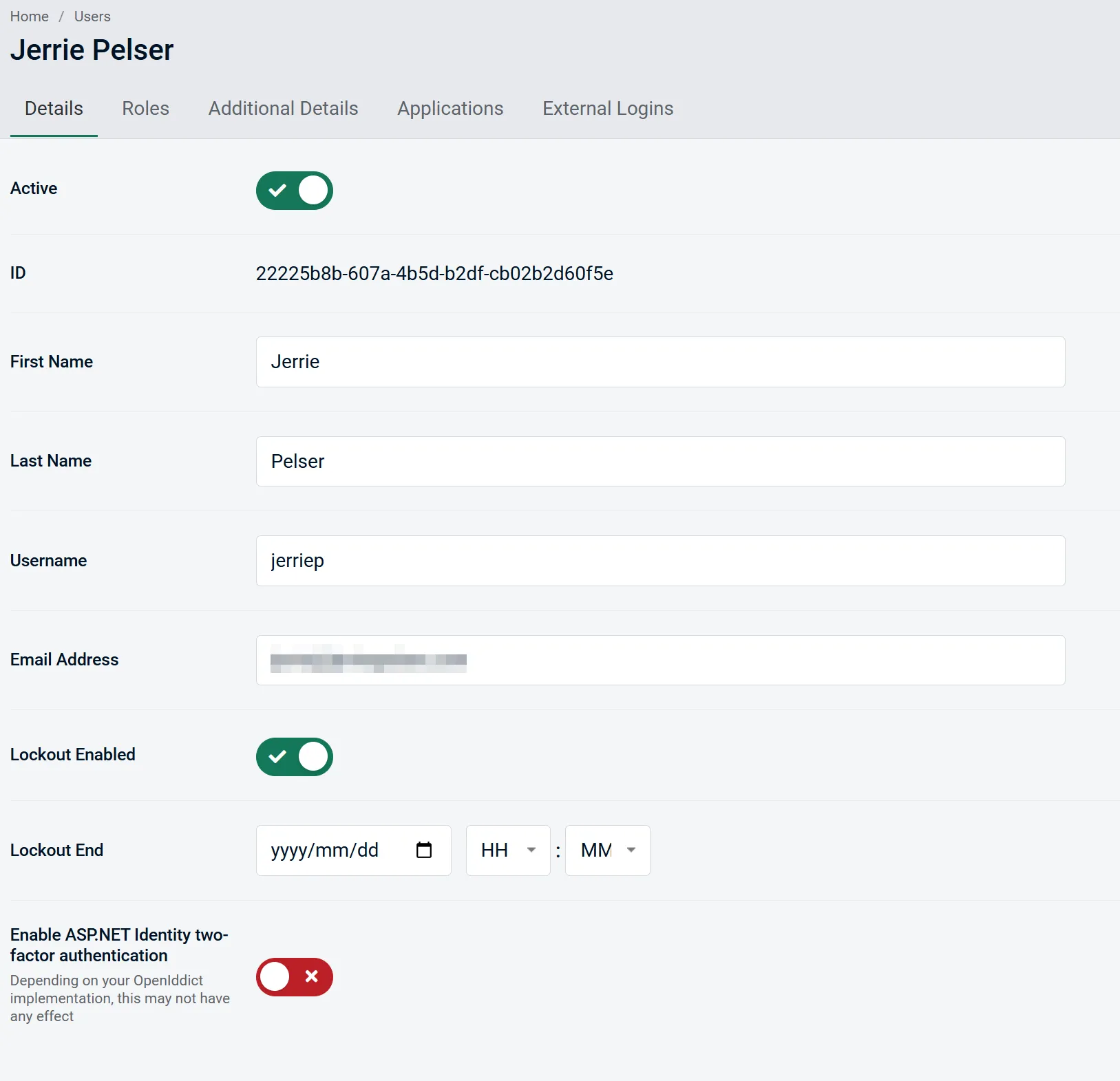
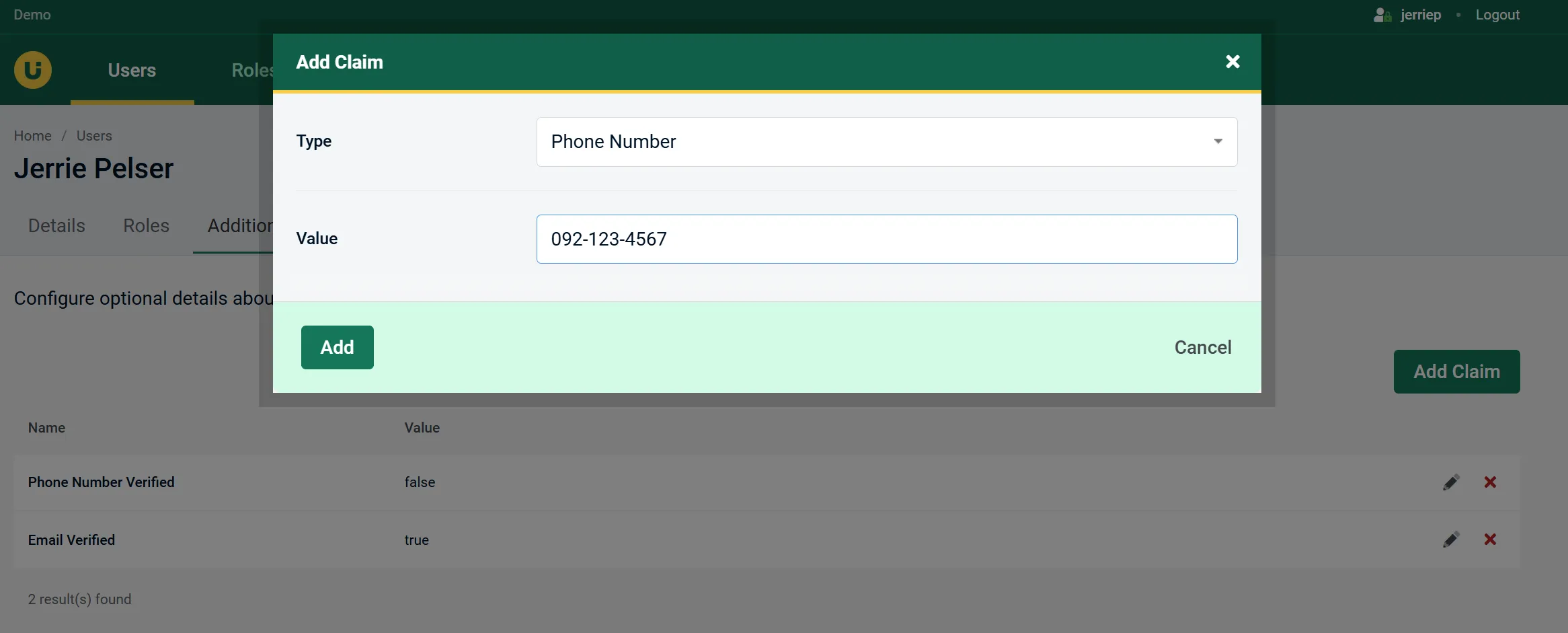
If you use Role-based authorization, you can also manage the roles in your application and assign users to specific roles.
Managing OpenIddict configuration
As mentioned previously, being able to manage users, roles, etc, is a by-product of the main focus of AdminUI - which is management of OpenIddict configuration.
When implementing an OpenIddict server, you typically need to configure various aspects of the server, such as the scopes, clients, APIs, etc. You have a few of options for managing these:
- The first option, which is used in the OpenIddict samples and documentation, is to create an
IHostedServiceimplementation that will create and configure the correct Clients. - The second option, would be to create your own Admin interface that would allow developers or admin users of your application to configure the OpenIddict Clients.
- Another option would be to create some sort of database migration that will create the correct entries in the OpenIddict database tables. This is probably the least favourite of the approaches as it requires intimate knowledge of the OpenIddict database structures and can become brittle over time as the underlying OpenIddict database structures evolved.
- The final option would be to use a 3rd party tool like AdminUI to manage all the OpenIddict configuration.
AdminUI provides you with a comprehensive user interface that allows you to manage the configuration of your OpenIddict server.
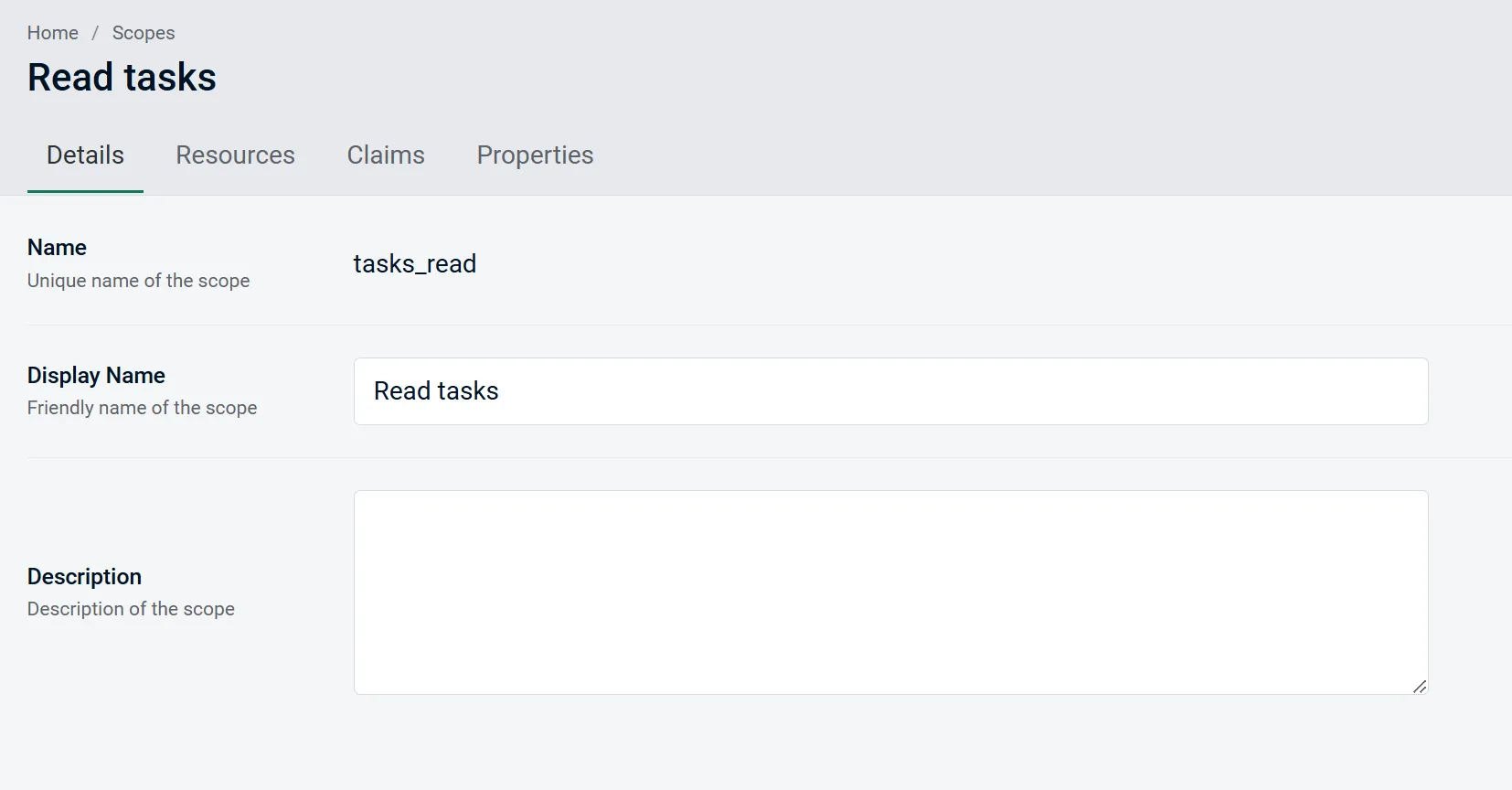
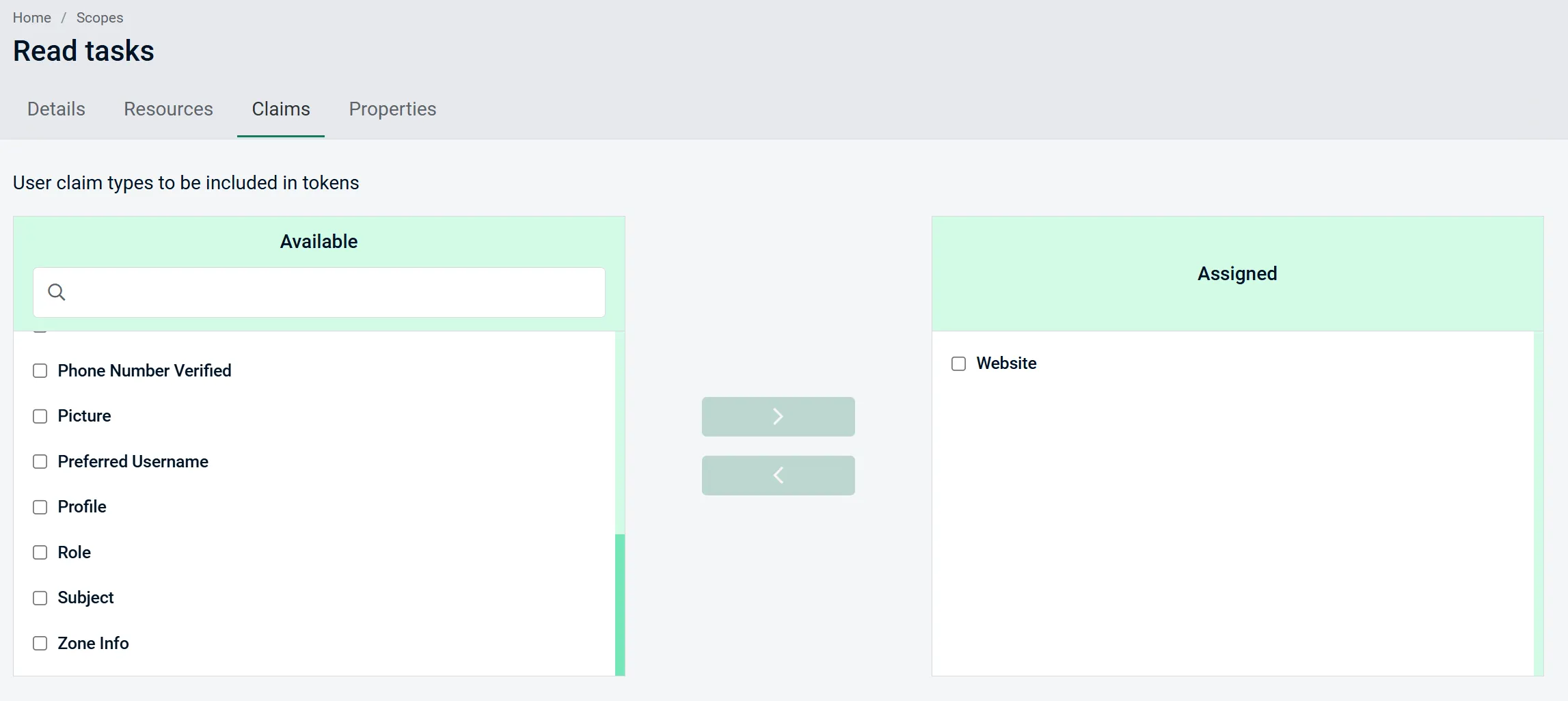
First off, it allows you to manage scopes and easily link resources and claims to the scopes.
You can also add Applications - whether those be APIs (resource servers) or Clients.
In both cases, they provide you with a wizard like interface. For example, when adding a new client, you can select the type of client and, based on the type of client you select, they will prompt you to configure the additional properties for that type of client.
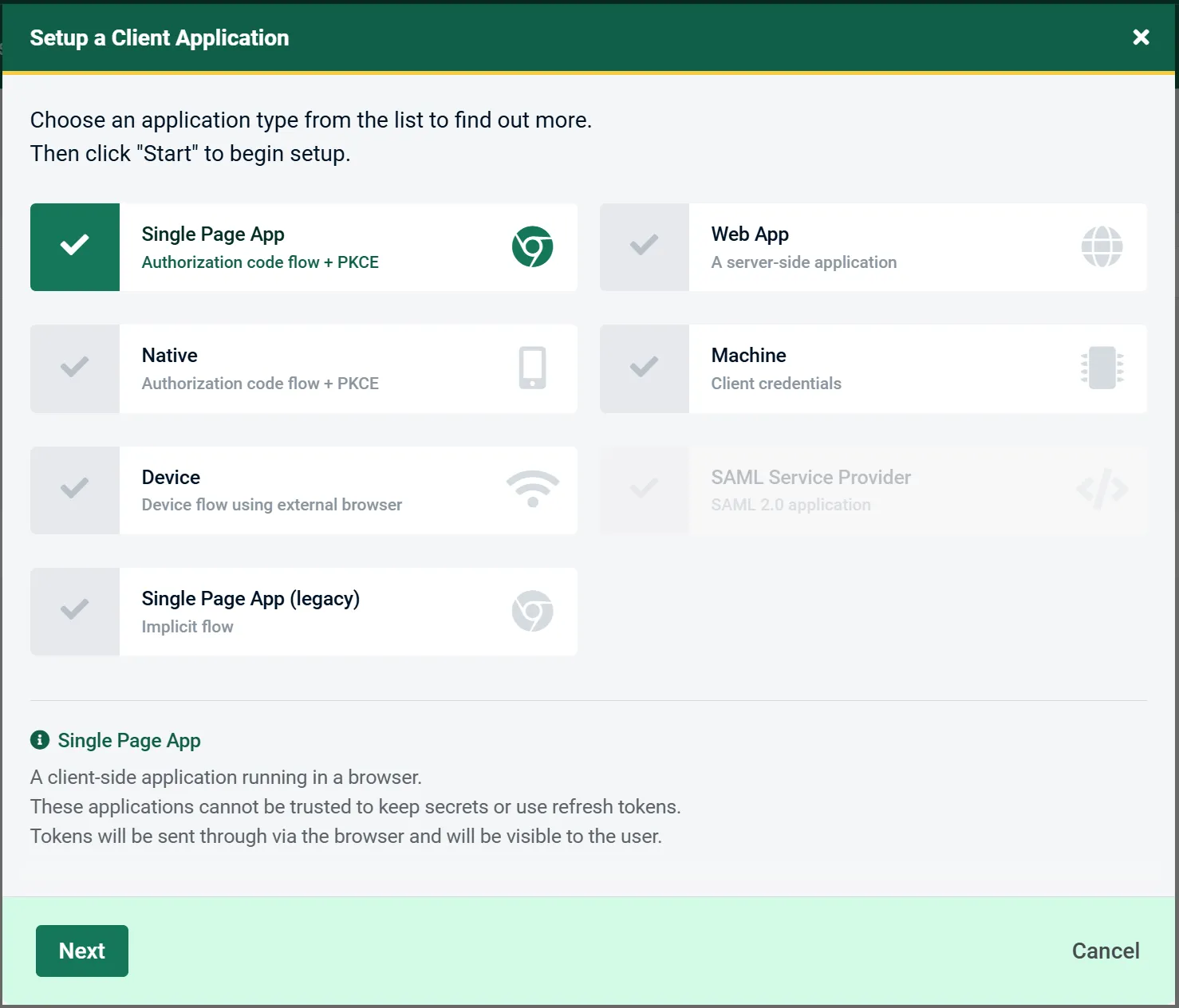
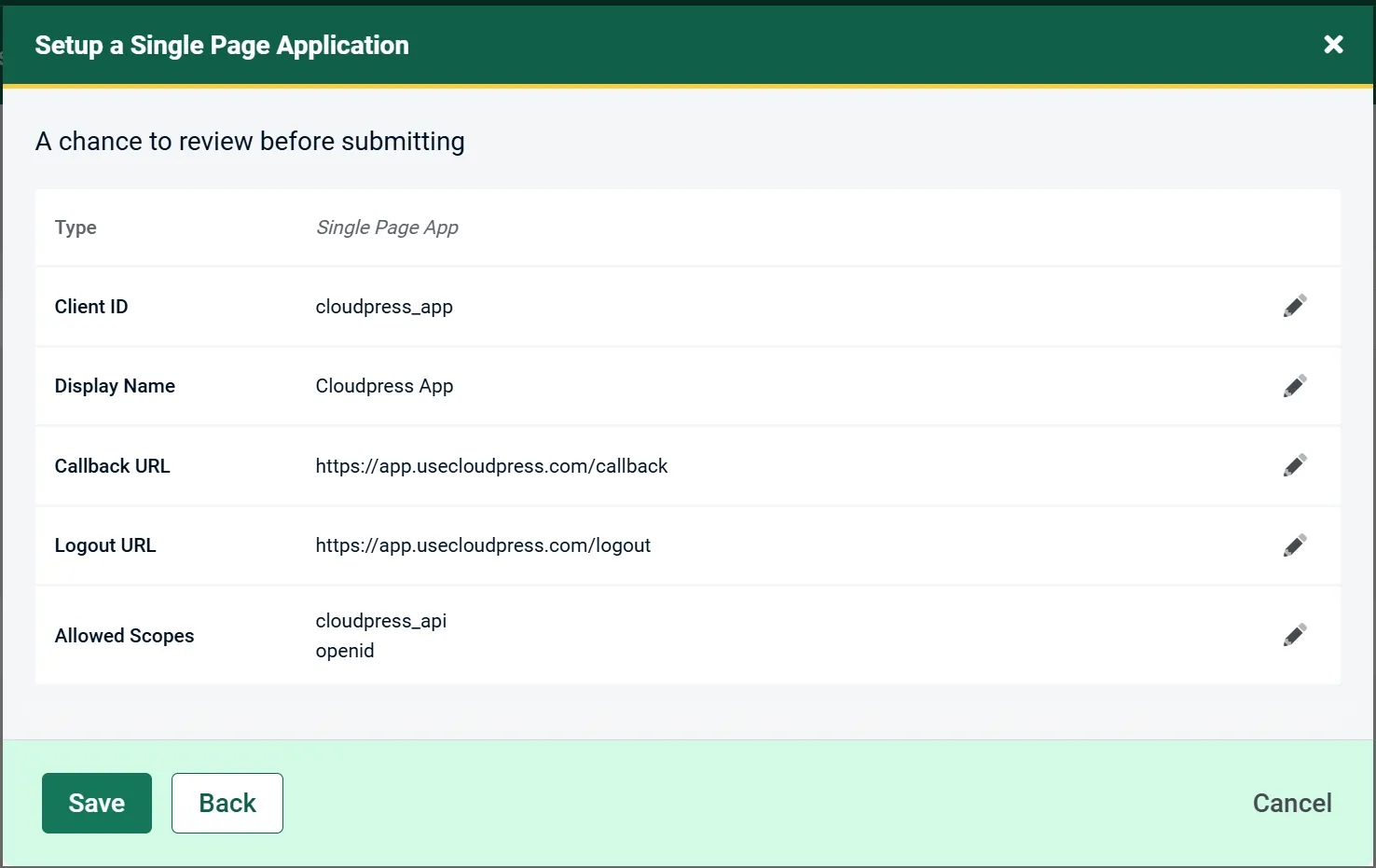
One advantage of the wizard interface is that AdminUI will ensure you add the required fields based on the type of application you create, and configure things like the client type and consent type in OpenIddict. This makes the process of adding an application less error-prone.
Downsides
OpenIddict supports various storage engines through its Entity Framework Core integration, MongoDB integration, and a few other third-party integrations. To achieve this, they abstracted the storage engine by declaring various IOpenIddictXxxStore interfaces which are implemented by these integrations.
AdminUI does not rely on these interfaces and rather implemented their own storage layer abstraction. Out of the box, they support SQL Server, MySQL, and PostgreSQL and also provide a sample implementation for MongoDB.
If you use another database for storage, or if you created your own custom storage provider for OpenIddict, you will need to do additional work to create a custom Identity Store for AdminUI. You can use the source code of their MongoDB provider as a starting point.
I doubt this will affect many people, but it is something to be aware of.
Conclusion
Overall I found that AdminUI provides an easy and convenient way for you to add user, role, and OpenIddict administration to your application. If you currently have to maintain a custom UI to do this, I suggest AdminUI as an alternative.
You can find more information and pricing for AdminUI from the AdminUI for OpenIddict product page.